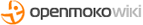Unbricking the Neo1973 (GTA01) without a debugboard
From Openmoko
(→Fixing the uboot partitions/environment) |
|||
| Line 181: | Line 181: | ||
| − | ===== Fixing the | + | ===== Fixing the NAND partitions/environment ===== |
You can try and skip this step but most likely you will need to run the dynpart command below to partition the NAND so dfu-utils knows where to put uboot in it. | You can try and skip this step but most likely you will need to run the dynpart command below to partition the NAND so dfu-utils knows where to put uboot in it. | ||
Revision as of 01:26, 21 July 2009
This page describes how to recover a Neo1973 (GTA01Bv4a) when the bootloader has been corrupted or wiped. The method described below does NOT use the official openmoko debug board and instead uses an easy to build alternative. This allows Neo1973 owners who have some skill in electronics to unbrick their phones without having to buy a costly debug board for a one-off unbricking.
Contents |
Precautions
Do not attempt this process until you have read this entire page and feel comfortable about all steps.
Require knowledge
The easy to build JTAG board described in this page requires some knowledge of electronic circuits and building them. If you don’t feel comfortable wiring up a circuit containing a few resistors, transistors and one integrated circuit you shouldn’t attempt to perform the unbricking method described below. Find someone who owns an official debug board or buy one yourself.
Soldering skills
This method requires you to solder a circuit together and also solder wires onto the Neo1973 PCB pads. These are small so require a steady hand. Soldering them is easier with a SMT tip on your iron but any small tip should work fine.
Care must be taken to not drip or flick solder onto the Neo1973 while working as this could put permanent marks on the LCD or short out components.
Wiring
Since this method requires connecting directly to the Neo1973 PCB incorrect wiring can easily damage the phone. All wiring should be triple checked before connecting the 3.3V power supply.
Be careful with the wires that you solder onto the Neo1973 PCB pads. These pads are small and do not require much force on the wires before the whole pad breaks off the PCB.
The circuit
The JTAG circuit required for unbricking a Neo1973 is relatively simple and requires 8 resistors, 1 IC, 1 transistor and 1 capacitor.
It is a modified version of the Olimex ARM JTAG clone found Here
NOTE: IC1A and IC1B are the same physical IC. The 74HC244N has 20pins.
It is recommended that this circuit be soldered together; a breadboard may work but could cause problems due to loose connections. The cable to the computers printer port should be kept short to reduce interference, 1 meter is fine.
Connecting the circuit to the Neo1973
The wires will need to be soldered to the Neo1973 pads. This should be done carefully with thin wire to reduce the strain on the pads. For a ground connection the metal GPS antenna cage nearby provides a usable ground point.
Installing the software required
To unbrick the Neo1973 using this circuit openocd is used to make a JTAG connection.
sudo apt-get install openocd
More information on installing/using openocd can be found here
openocd requires a config file, copy the following into a file called openocd.cfg and put it into the folder where you're going to be running openocd from.
#daemon configuration telnet_port 4444 gdb_port 3333 #interface interface parport parport_port 0 parport_cable wiggler jtag_speed 15 #use combined on interfaces or targets that can't set TRST/SRST separately reset_config trst_and_srst #srst_pulls_trst #jtag scan chain #format L IRC IRCM IDCODE (Length, IR Capture, IR Capture Mask, IDCODE) jtag_device 4 0x1 0xf 0xe #target configuration daemon_startup attach #target <type> <startup mode> target arm920t little reset_run 0 arm920t #working_area 0 0x200000 0x4000 backup run_and_halt_time 0 5000 #flash configuration (K9D1208V0M: 512Mbit, x8, 3.3V, Mode: Normal, 1st gen) #NOR flash configuration (SST39VF400A 4Mbit, x16, 3.3V, 128sect, 4k/sect, 8 blocks (64kByte per block) # flash bank cfg addr length chip_width bus_width target flash bank cfi 0x00000000 0x80000 2 2 0
NOTE: This config file has the word NOR which implies it's for GTA02, however it worked fine for me on GTA01
You will also need a copy of the uboot and lowlevel binaries which can be found here.
wget http://downloads.openmoko.org/distro/releases/Om2008.12/gta01bv4-lowlevel.bin wget http://downloads.openmoko.org/distro/releases/Om2008.12/gta01bv4-u-boot.bin cp gta01bv4-lowlevel.bin /tmp/lowlevel.bin cp gta01bv4-u-boot.bin /tmp/uboot.bin
The unbricking process
To unbrick the phone a new uboot needs to be flashed, however to do this uboot needs to be running. To get uboot running again a copy of uboot needs to be uploaded to the phone memory over JTAG and executed. Then you can get access to /dev/ttyACM0 again and use dfu-util to flash a good copy of uboot.
Pre checks
Before continuing check the following is done.
![]() The circuit above is assembled and checked
The circuit above is assembled and checked
![]() It is wired to the Neo1973 PCB pads correctly
It is wired to the Neo1973 PCB pads correctly
![]() It is connected to the computers printer port and the port is enabled in the bios (parport is used)
It is connected to the computers printer port and the port is enabled in the bios (parport is used)
![]() The circuit has 3.3V power from an external power supply
The circuit has 3.3V power from an external power supply
![]() The battery is charged (this may/maynot work with the usb power connected)
The battery is charged (this may/maynot work with the usb power connected)
Loading uboot into memory over JTAG
Now start openocd
sudo openocd
If everything is setup and connected correctly openocd should start. If you get errors check your circuit and printer port. You can also try plugging and unplugging the usb cable to the phone (Doing this seems to reset something and allow openocd to start sometimes)
If openocd is running correctly you should be able to open another shell and telnet to it.
telnet localhost 4444
With the telnet session open the following commands should load a new lowlevel and uboot into memory and run them.
- Reset and halt the cpu at PC=0
> reset halt target halted in ARM state due to debug request, current mode: Supervisor cpsr: 0x400000d3 pc: 0x00000000 MMU: disabled, D-Cache: disabled, I-Cache: disabled
- Download a small piece of code for low-level SDRAM timing initialization (overwrite 4k SRAM of steppingstone)
> load_binary /tmp/lowlevel.bin 0 downloaded 332 byte in 0s 21899us
- Assert a break point at address 0x33f80000 (which indicates that the low-level code has finished)
> bp 0x33f80000 4 hw breakpoint added at address 0x33f80000
- Run the code up to the break point
> resume Target 0 resumed > Target 0 halted target halted in ARM state due to breakpoint, current mode: Supervisor cpsr: 0x600000d3 pc: 0x33f80000 MMU: disabled, D-Cache: disabled, I-Cache: enabled
NOTE This next step may take a while (around 250seconds), the openocd.cfg file on this page has had the speed slowed right down to reduce errors (jtag_speed 15). The speed of 15 seems to work even when the circuit is made on breadboard with wires everywhere :)
- Download the u-boot RAM image to 0x33f80000
> load_binary /tmp/uboot.bin 0x33f80000 downloaded 135692 byte in 6s 567264us
- Resume processing
> resume Target 0 resumed
At this point the uboot text should be showing on the Neo1973 LCD. If not, try again, it can take a few tries.
Connect the USB cable at this point if not already connected.
Fixing the NAND partitions/environment
You can try and skip this step but most likely you will need to run the dynpart command below to partition the NAND so dfu-utils knows where to put uboot in it.
cu -l /dev/ttyACM0
GTA01Bv4 # dynpart mtdparts mtdparts=gta01-0:0x00030000(u-boot),0x00004000(u-boot env),0x00208000(kernel),0x00400000(initrd),0x039c4000(rootfs) GTA01Bv4 # dynenv set u-boot_env 45 4e 56 30 - 00 00 03 00 GTA01Bv4 # saveenv Saving Environment to NAND... Erasing Nand...Writing to Nand... done
Flashing a new uboot
At this point all that’s left to do is to flash a new uboot to NAND which will unbrick your Neo1973.
sudo ./dfu-util -a u-boot -R -D /tmp/uboot.bin
Your Neo1973 is now unbricked :)
The process will probably have reset the uboot environment to a very basic default with only one option to boot from NAND.
Menu items to boot from SD will have to be re-added. See here
Final thoughts from the author
![]() It may be possible to use this simple JTAG circuit for actual debugging. I don’t know enough about JTAG debugging to be sure.
It may be possible to use this simple JTAG circuit for actual debugging. I don’t know enough about JTAG debugging to be sure.
![]() This JTAG circuit should also work for the Neo Freerunner (GTA02) however the PCB pads may be in a different location and would need checking.
This JTAG circuit should also work for the Neo Freerunner (GTA02) however the PCB pads may be in a different location and would need checking.
![]() Thanks to Paul Fertser for helping me to unbrick my neo1973 :)
Thanks to Paul Fertser for helping me to unbrick my neo1973 :)